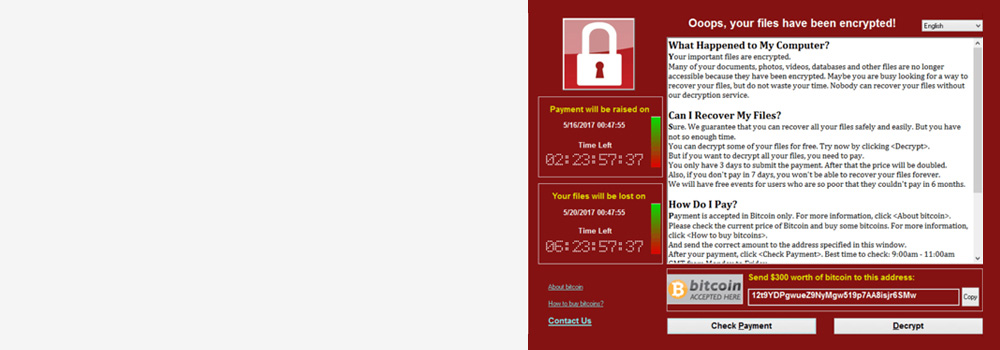
Welcome to Cardiff Data Recovery – Wales’s No.1 Forensic Ransomware Data Recovery Specialists, with over 25 years of investigative experience. Our dedicated forensic team specialises in recovering data from systems affected by ransomware attacks, including encrypted hard drives, system lockdowns, partially encrypted files, and inaccessible storage.
If you’ve fallen victim to ransomware – whether through email phishing, malicious downloads, or server compromise – our data recovery services ransomware specialists are here to help.
🔐 What We Recover From
We provide professional ransomware decryption and data recovery services from:
- Laptops and desktops (Windows, macOS, Linux)
- External hard drives and USB flash drives
- RAID arrays and NAS systems (RAID 0, 1, 5, 10, etc.)
- Virtual machines (VHD/VHDX, VMDK)
- Servers and cloud-connected environments
We handle all major ransomware variants including:
- WannaCry
- LockBit
- REvil (Sodinokibi)
- Conti
- Maze
- BlackCat (ALPHV)
- Ryuk
- Clop
- Dharma
- DarkSide
🧠 Our Top 20 Techniques for Ransomware Decryption & Data Recovery
- Ransomware Identification
Analysing encrypted file extensions, ransom notes, and encryption patterns to determine the ransomware strain. - Known Decryptor Matching
Using secure repositories and tools to match the strain with publicly available decryptors (when applicable). - Custom Scripted Decryption
Writing custom scripts for partial or flawed encryption algorithms. - Brute Force Key Recovery
Exhaustive key permutation methods for weakly encrypted data sets. - Forensic File Carving
Extracting raw file signatures from encrypted drives where metadata is lost. - Recovery via Shadow Copies
Attempting to restore from Volume Shadow Copies, if untouched by the attacker. - Partition & File System Repair
Repairing corrupted partitions to regain access to encrypted or partially encrypted files. - Partial File Reconstruction
Rebuilding usable file content from partially encrypted or fragmented files. - Mirror and Backup Recovery
Analysing alternate storage locations, disk clones, and backups for unencrypted data. - Block-Level Analysis
Deep forensic block-by-block inspection of encrypted volumes to identify accessible data areas. - System Rollback Recovery
Attempting recovery via safe rollback where system restore points are available. - Network Drive & Cloud Sync Restoration
Examining cloud-synced services (OneDrive, Dropbox) for pre-encrypted file versions. - Log File Forensics
Investigating file access history and encryption timelines for file recovery prioritisation. - Encrypted File Header Mapping
Reconstructing known file headers and footers (e.g., for PDFs, JPEGs, DOCX). - Decryption via Private Key Negotiation
In rare cases, working with clients to legally and securely negotiate for decryption keys. - Comparative File Analysis
Comparing infected and clean file samples to reverse-engineer the encryption logic. - Ransomware Flaw Exploitation
Identifying weaknesses in known ransomware encryption routines. - Registry & Temp File Analysis
Extracting key material or executable paths from local registry hives and temp folders. - Live RAM Capture and Analysis
Analysing live memory snapshots for decryption keys left in RAM during encryption. - Manual Hex-Based Recovery
Using low-level hex editors to identify recoverable segments within encrypted files.
💻 Supported Systems
We support ransomware recovery across:
- Windows 11 / 10 / 8 / 7 / Server 2016–2022
- macOS Monterey, Ventura, Big Sur and older
- Linux distributions (Ubuntu, CentOS, Debian, Red Hat)
- VMware, Hyper-V, VirtualBox-based systems
- RAID-based NAS devices (QNAP, Synology, Netgear ReadyNAS, Buffalo, etc.)
✅ Why Choose Cardiff Data Recovery?
- Over 25 years of forensic data recovery experience
- Successful recovery from thousands of ransomware cases worldwide
- In-house forensic lab for secure, confidential recovery
- Compliance with GDPR and law enforcement cooperation where needed
- No recovery = no data charge (free diagnostic)
- Emergency 48-hour critical recovery option available
We’ve worked with businesses, government departments, solicitors, medical practices, and financial institutions across the UK and internationally.
📞 Contact Cardiff Data Recovery Today
If your files have been encrypted or locked by ransomware, don’t delay. Time is critical — the sooner we start, the higher the recovery success rate.
Contact Cardiff Data Recovery today for a free diagnostic. Our specialist forensic engineers are ready to assist with secure, discreet, and expert data recovery services ransomware victims can rely on.